
How to Protect your Cryptocurrency from Scams
The cryptocurrency market has become increasingly treacherous. With several billion dollars in inflows, scams tied to cryptocurrencies are escalating in 2024, marking one of the largest areas of illicit activity year-to-date.
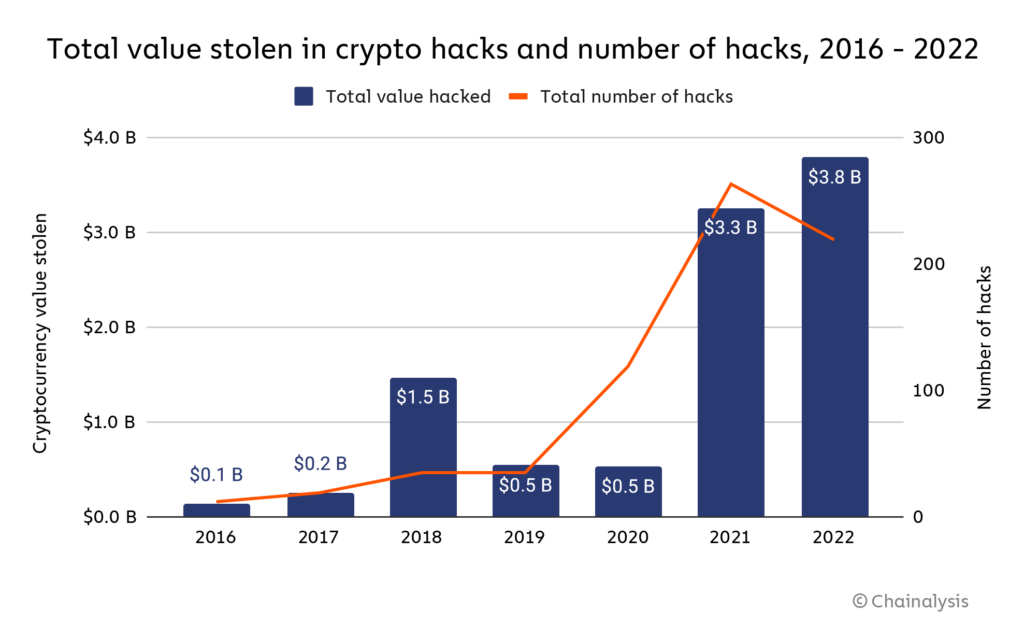
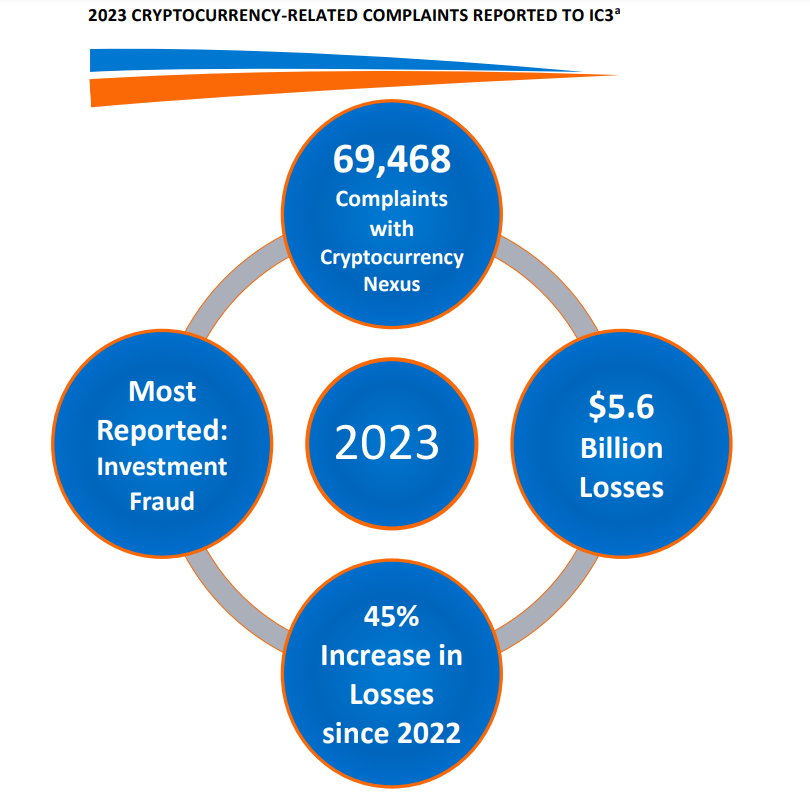
A significant trend in this year's scam landscape is the rapid evolution of scammers' on-chain activities and their off-chain tactics, including the manipulation of domains and social media accounts. With scammers developing ever more sophisticated methods to separate investors from their digital assets, there's no wonder that the Better Business Bureau (BBB) has classified cryptocurrency scams as the riskiest type of fraud in the United States, with a shocking 80% of targeted individuals losing money. They also reported more than 67,000 scams in 2023, across both the U.S. and Canada, while blockchain analytics firm, Chainalysis,documented a staggering $3.8 billion stolen through various crypto schemes solely in 2022.
Can you imagine how much those numbers have grown in 2024???
This comprehensive guide will explore the most common cryptocurrency scams and provide detailed strategies to protect your digital assets.
Table of Contents
-
Understanding Common Crypto Scams
- Proximity Scams
- Impersonation Scams
- Phishing Attacks
- Malware Attacks
- Crypto Investment Scams
-
Essential Security Practices in Crypto
- Wallet Security
- Transaction Safety
- Network Security
- Account Protection
- Social Engineering Defense
- 10 Quick Tips on how to Avoid Cryptocurrency Scams
- BONUS: 20 Crypto Red Flags to watch out for
- Trade Safely with TOKERO
- Conclusion

Much like the early days of the internet, where scams ran rampant and regulations were scarce, the cryptocurrency market is still in its infancy. Foundations are being built, but with innovation comes risk, and bad actors have seized this opportunity to exploit the inexperienced. Investors, drawn in by the promise of revolutionary technology and quick profits, must exercise caution. As the old saying goes, "If it's too good to be true, it probably is."
The last few years have shown just how risky the crypto space can be, with several high-profile collapses wiping out billions. But despite these challenges, millions of people use crypto every day.
The key is knowing how to protect yourself, and that's exactly what this guide will help you do - how to keep your coins secure, how to DYOR (do your own research), how to identify scams and how to protect yourself from scams in crypto.
Knowledge is your best defense against becoming the next victim so let's start this article with the most common scams you can find in crypto.??
I. Understanding Common Cryptocurrency Scams
1. What are Proximity Scams?
One of the most alarming emerging trends is the "proximity breach" scam. Unlike traditional scams where criminals are unknown entities, these attacks come from trusted individuals within victims' inner circles.
Types of Proximity Scams:
Friends & Family Scams
In a recent high-profile case, a crypto CEO lost $450,000 after simply connecting to his "best friend's" WiFi network. Similar cases have involved family members stealing significant amounts through close access to victims' devices.
Romance Scams
Amongst the best revenue generating machines for scammers is the romance scam, with one Myanmar-based compound netting at least $101.22 million YTD by Q1 2024.
In this type of scam, a con artist builds a fast-moving relationship with someone they've met online, often professing love early on to create a deep emotional bond. Once they've gained the victim's trust, the scammer typically starts making requests for money, using various tactics. They may begin distancing themselves, explaining that financial troubles or a need to care for an ill family member prevent them from being closer. In other cases, the scammer may express a desire to meet in person but claim they can't afford travel expenses, prompting the victim to help financially.
Quick Tips on how to identify proximity scams:
- If someone randomly sends you a message and wants to get to know you better.
- If someone advances their relationship with you very quickly.
- If someone you know is urgently pressing you to buy into a token you don't know about or to use a certain website.
- If someone shares a lot of personal stories fast to gain your sympathy in order to manipulate you to send them money.
How to prevent proximity crypto scams:
- Think rationally when someone seems suspicious to you. Don't brush it off saying "eh, it won't happen to me", because that's when it will happen to you.
- Don't use the same phone or laptop that you use for cryptocurrency elsewhere than your home. Having a backup phone that you can use in your day-to-day life will save you a lot in the long run.
- Don't venture into fast developing relationships if you haven't even seen the person once.
- Beware messages from unknown people. This is rule #1 in all of crypto. Be suspicious of everybody.
- Don't click links unless you have thoroughly verified the domain and are sure the person sending it is legit.
2. Impersonation Scams

In the crypto world, impersonation frauds often take place in stages. Scammers often pose as celebrities, influential figures, or reputable cryptocurrency platforms to craft convincing online personas. Using these fake online identities, they engage with potential victims, gaining trust through persuasive language and fabricated credentials. Under the guise of investment opportunities, they prompt victims to send cryptocurrency or divulge personal information to complete the scam. Once victims comply, the scammers swiftly disappear with the funds or stolen data.
Types of Impersonation Scams:
Cryptocurrency Exchange Staff Impersonators:
Criminals impersonate cryptocurrency exchange support staff, alerting users to supposed urgent issues with their accounts to instill a false sense of emergency. This pressure tactic is designed to deceive victims into providing login credentials or clicking on malicious links.
Celebrities Impersonators and Giveaway scams
Changing the sphere of influence, scammers may also try to pose as celebrities, successful business people, or cryptocurrency influencers. To capture the attention of potential targets, many scammers promise to match or multiply the cryptocurrency sent to them in what is known as a "giveaway scam."
Well-crafted messaging from what often looks like an existing social media account can create and spark a sense of validity and urgency. This "once-in-a-lifetime" opportunity can lead people to transfer funds quickly in hopes of receiving an instant return.
Cryptocurrency Token Impersonation Scam and Address Poisoning Attacks
The FBI Denver reports a rise in cryptocurrency scams where criminals create imitation tokens resembling well-known ones like Tether (USDT) and send them to victims via lookalike addresses, a tactic known as an address-poisoning attack. By exploiting wallet software that only displays parts of the address, scammers deceive victims into mistaking these fake tokens for legitimate assets. Victims often don't realize the tokens are worthless until they attempt to redeem them.
In one case identified by the FBI, a Colorado resident lost $2.1 million in a scam involving fake stablecoins and was later "fined" under false pretenses. The FBI advises users to carefully verify full wallet addresses.
Quick Tips on How to Identify Crypto Impersonators:
- If they send you urgent account security notices such as expiration, breaches, password changes etc.
- If they use pressure tactics and time limits to create a sense of urgency
- If they contact you on unofficial communication channels such as Telegram, WhatsApp.
- If they have many grammatical errors or ask for sensitive personal information either directly or via a link they send you.
How to Protect Yourself from Impersonation Scams:
- Be wary if you discover frequent grammatical and spelling errors.
- Always doubt an offer's veracity if it seems unreasonably profitable.
- Never give your personal data or private keys to anyone, no matter who they say they are. This is a serious red flag. Trustworthy cryptocurrency businesses and services won't ask for this information.
- Make sure the website domain is the correct, official one by checking it twice.
- Carefully consider the matter if you receive unsolicited texts urging you to invest or take hasty action.
3. Phishing Attacks
In this crypto scam, attackers create fake websites or fake emails that mimic legitimate ones, tricking users into entering their private keys. Once scammers obtain this sensitive information, they steal the victim's cryptocurrency.
For example, a user may receive an email that looks like it's from their wallet provider, directing them to a fake site to enter their private key. Phishing is the most common consumer attack; in 2022 alone, over 300,000 people fell victim, losing a total of $52.1 million to such scams, according to the FBI.
Quick Tips on How to Identify a Phishing Attack:
- If the messages stress urgency, such as "Act now!" or "Your account will be locked," that rush you into clicking.
- If they have poor grammar, odd wording, or unusual formatting.
- If they ask for personal information, private keys, or account details through email.
How to Protect Yourself from Phishing Attacks:
- Look for slight misspellings or extra characters in the sender's email address, which often indicate a fake email.
- Hover over any links without clicking to see the actual URL. Phishing links often resemble legitimate sites but with slight variations. Additionally, only access important sites by typing the URL directly into your browser instead of clicking on links from emails or messages.
4. Malware Attacks

The rise of crypto malware has reached staggering levels, with over 300 million attacks recorded in just the first half of 2023 - a nearly 400% increase from the same period in 2022. This rapid escalation reflects a shifting strategy among cybercriminals who are increasingly focusing on crypto malware attacks over more disruptive methods like ransomware. The rise of the Internet of Things (IoT) has also played a significant role in this surge. IoT devices typically lack strong security protections, leaving them especially vulnerable to cryptojacking attacks. As a result, these devices have widened the attack surface, giving hackers even more targets for crypto malware operations.
Types of Crypto Malware Attacks:
Crypto Malware
Crypto-malware allows hackers to run cryptojacking on other people's computers. Although cryptomining by itself is a legitimate process, when carried out through malware, it uses another user's devices and processing power without their consent, depleting their resources without any benefit to the owner.
This type of malware generally doesn't steal data but continuously mines cryptocurrency in the background on the infected device. It can appear as legitimate software, often embedding itself into other applications to run inconspicuously anytime the device is in use. An advanced way of spreading crypto-malware is through "drive-by" downloads. If a user visits a compromised website, the malicious code begins running on their device without being saved to their system, making it even harder to detect.
Ransomware
Both ransomware and crypto-malware generate income for cybercriminals, but they operate differently. Ransomware encrypts the victim's data and demands payment in exchange for the decryption key. If the ransom isn't paid, attackers may sell the stolen data on the dark web. The average ransom payment in 2022 was $4.7 million.
Quick Tips on How to Identify a Malware Attack:
- If your device slows down significantly or heats up unexpectedly, it may be overworking due to hidden crypto mining.
- If you notice spikes in CPU usage even with minimal activity, that's often a sign of cryptojacking.
- Look for any unusual applications or browser extensions that you don't remember installing.
How to Protect Yourself from Malware Attacks:
- Install reputable antivirus software that specifically detects cryptojacking scripts and malware.
- Keep your software updated, as many attacks exploit older versions of software with known vulnerabilities.
- Use browser extensions that block cryptojacking scripts, such as MinerBlock, which prevent websites from running hidden cryptomining code.
5. Crypto Investment Scams

Their method follows the playbook of many standard scams: They send an email with links that lead holders to a specially created website and ask them to enter private keys. Once the hackers have this information, they steal the victim's cryptocurrency.
Crypto-based investments, such as initial coin offerings (ICOs) and non-fungible tokens (NFTs), provide even more avenues for scammers to access your money.These schemes often involve elaborate marketing campaigns and celebrity endorsements. The median loss in investment scams is $3,800, though many victims lose substantially more.
Types of Crypto Investment Scams:
Rug Pulls
The term "rug pull" originates from the expression "pulling the rug out from under someone," reflecting the sudden and deceptive nature of this scam. Rug pulls are schemes that seem legitimate and promising, but once investors contribute substantial funds, the project creators abruptly withdraw all the funds, disappearing without a trace.
Rug pulls have been pervasive across the crypto ecosystem, especially in sectors like decentralized finance (DeFi), non-fungible tokens (NFTs), Web3, and various metaverse projects. In 2021 alone, rug pulls drained an estimated $2.8 billion in cryptocurrency from unsuspecting investors, comprising 37% of all crypto scam revenue that year, according to Chainalysis.
A so-called rug pull occurs when project members raise capital or crypto to fund a project and then suddenly remove all the liquidity, and they themselves disappear and become unreachable. Scammers abandon the project, and investors lose all they have contributed. Such as The Bored Bunnies NFT scheme that raised $20 million before abandoning development.
Fake ICOs
Unlike initial public offerings (IPOs), which are tightly regulated, initial coin offerings (ICOs) only require a white paper and a few enticing features – such as low entry barriers, potential for rapid growth, lack of geographical restrictions, and simple validation processes. Given this, it's unsurprising that the ICO market has seen a period of tremendous growth. Research indicates that between January 2016 and August 2019, ICOs raised nearly $13 billion globally.
For example, in 2014, Ruja Ignatova, known as the self-styled "crypto queen," and her team launched a Bulgaria-based cryptocurrency venture called OneCoin Ltd. Ignatova and her associates allegedly made deceptive claims about the coin's value to attract investors. She disappeared, and the exchange unexpectedly shut down in 2017. The platform is estimated to have defrauded victims of over $4 billion.
Despite the attractive advantages of ICOs, they present considerable risks for investors. A 2018 report from Satis Research Group examined around 1,500 ICOs, revealing that 78% of them were scams, collectively valued at $1.3 billion.
Ponzi Schemes
A "Ponzi scam" is another common type of fraud found in the ICO landscape. This scheme generally involves requiring investors to put money into a product or service associated with the ICO, with promises of high returns at a later stage. Similar to a pyramid scheme, Ponzi schemes use funds from new investors to pay earlier backers. While pyramid schemes rely on recruiting new participants by rewarding early adopters, they inevitably collapse once the pool of potential recruits runs dry.
Despite the specific technology involved, most Ponzi schemes share certain characteristics. The Securities and Exchange Commission (SEC) has flagged several warning signs to help investors spot such schemes.
One recent example involves Trendon T. Shavers, the alleged operator of a Bitcoin Ponzi scheme, who promoted a Bitcoin "investment opportunity" on an online Bitcoin forum. Investors were promised up to 7% interest per week, supposedly generated through Bitcoin arbitrage activities. Instead, the invested Bitcoins were allegedly used to pay earlier investors, while some were converted to U.S. dollars to cover the organizer's personal expenses.
Pump & Dumps
A "pump and dump" scheme is another tactic used by scammers that can be difficult to spot right away. This scheme works by asset holders falsely promoting and hyping an asset to attract buyers, driving up the price. Once the price peaks, these holders sell off their overvalued shares at a profit, causing the price to crash and leaving recent buyers with a worthless asset.
An example is the E-Coin incident: on February 6, 2018, this little-known cryptocurrency skyrocketed by 4,742% in just one day, leaping from near the bottom of the TOP-500 in market capitalization to a spot in the TOP-20. This meteoric rise happened during a stagnant cryptocurrency market, with Bitcoin even dropping below $6,000. Yet investors flocked to E-Coin despite its obscurity. Its flat performance chart throughout 2017 - even during a strong market rally - suggested it had little real appeal or genuine investor interest, raising questions about the sudden surge.
Quick Tips on How to Identify a Crypto Investment Scam:
- If they promises high, guaranteed returns with minimal risk
- If they promise a steady stream of returns, unaffected by market conditions
- If sellers lack proper licenses to sell investment products or are not registered with the SEC
- If they disguise their token sale progress through private addresses, making it hard for investors to gauge funds raised or time remaining.
How to Protect Yourself from Crypto Investment Scams:
- Conduct in-depth research on the individuals behind the project. If you can't find any information about a developer or founder on LinkedIn, X or other social platforms, it's a red flag. Even if profiles are available, check if their level of engagement matches their followers and likes; if they have a massive following but low activity, the accounts may be fake.
- Look for additional materials such as financial models, legal considerations, SWOT analysis, and a clear implementation timeline in the project's Whitepaper.
- Look for companies that aim to keep potential investors up to date with regular, detailed progress reports on a company website or on social media. It's also useful to look if a company has a timeline for what has taken place in the development process, as well.
- Some (not all) scams will often lazily imitate features from other popular projects, signaling that the project may not have originality or long-term value for investors
- Check if the project's token is on known centralized marketplaces like Binance or Coinbase, which have certain standards in place and only list assets that are legal and safe, though their listings are not an indicator of quality or potential for gains.
- Review the asset's price trends and development milestones. A price trend in line with the general market is typical, while sudden spikes without reason could be signs of manipulation.
- Exercise caution with coins worth only a fraction of a cent, as these are often easier to manipulate.
- Avoid investing in new startups or penny stocks without a solid history; established projects take time to develop and prove their value.

With so many types of cryptocurrency scams happening, some may wonder: Is crypto a con? Is Bitcoin a scam? Short answer - No. Crypto itself is not inherently a scam; rather, it is as safe as the measures you implement to protect yourself.
So, how can you save yourself from crypto scams and protect your crypto assets? Follow these steps:
II. Essential Security Practices in Crypto
1. Wallet Security: Use a Secure Wallet
Hardware Wallets:
For long-term storage, a hardware wallet (like Ledger or Trezor) is one of the most secure options. These physical devices keep your private keys offline, making them difficult for hackers to access.
Software Wallets:
If you use a software wallet (such as MetaMask or Phantom), choose one with robust security features and a good reputation. Keep the software updated and only download from official sources.
Cold Wallets:
Consider moving assets you don't need immediate access to into a cold (offline) wallet, which isn't connected to the internet, further reducing hacking risks.
5 Tips on how to keep your crypto wallet safe:
- Use hardware wallets for significant holdings.
- Never share private keys or seed phrases. It's best to note them down on a piece of paper and keep that paper.
- Keep backup phrases offline in secure locations, it's best in 2 (or more) different locations at the same time.
- Regularly audit wallet permissions and revoke unnecessary access.
- Use cold storage for assets you don't need to access regularly.
2. Transaction Safety
Verify the Full Address:
Double-check every character of the recipient's address to avoid mistakes or potential scams. When sending cryptocurrencies, copy and paste the recipient address or use a QR code. ALWAYS double-check. Check the first and final few characters of the address to make sure it's the correct one. Additionally, you may want to use a domain like ENS to make it easier for people to send you crypto.
Use Test Transactions:
When transferring a large amount, start with a small test transaction to verify the process.
Enable Whitelisting:
Many exchanges allow you to whitelist trusted wallet addresses, adding an extra layer of security.
Multi-Signature Transactions:
Set up multi-signature requirements for significant transactions, ensuring that multiple parties or devices authorize each transaction.
3. Network Security
Avoid Public WiFi:
Public networks are often unsecured and make it easier for hackers to access sensitive information. Connect only through secure, private WiFi. At home, disable WiFi Protected Setup (WPS), as it poses security risks. WPS was designed for quick and easy device connections, but it leaves your router vulnerable. Instead, enable WPA2 encryption on your WiFi for stronger protection. If WPA2 isn't an option, use WPA. Avoid using WEP encryption, as it is less secure.
Use a VPN:
A Virtual Private Network (VPN) helps encrypt your online activity and can add a level of security when accessing crypto accounts.
Keep Devices Updated:
Regularly update your devices with the latest security patches to defend against known vulnerabilities.
Install Reputable Antivirus Software:
Use a trusted antivirus program to protect against malware and other malicious attacks.
4. Account Protection
Enable 2FA using hardware keys when possible:
Always enable 2FA on crypto exchanges and wallet apps. This adds an extra layer of security, requiring a second code from an app like Google Authenticator or Authy, which cybercriminals would need to access in addition to your password.
Use Unique, Complex Passwords:
Create strong passwords for each platform, avoiding reuse across accounts.
Never Store Seed Phrases Digitally:
Seed phrases should be stored offline, in secure physical locations to reduce the risk of unauthorized access.
Monitor Account Activity:
Regularly check for unauthorized access or activity in your crypto accounts.
5. Social Engineering Defense
Never Share Credentials:
No legitimate support staff or crypto service will ask for your credentials. Keep login and wallet information private.
Verify Communication Channels:
Always confirm messages or requests through official channels, and be wary of unusual requests or prompts to send funds.
Be Skeptical of Investment Advice:
Avoid unsolicited advice from unknown sources, especially for new or unproven projects.
Research New Projects Thoroughly:
Before investing in new projects, research thoroughly, and ensure legitimacy to avoid scams.
I know, it's a lot to take in so let's make it easier:
III. 10 Quick Safety Tips on how to Avoid Cryptocurrency Scams:

- Never Share your Private Crypto Keys
- Keep your private keys secure; sharing them grants others access to your funds. Legitimate transactions don't require your private key.
- Avoid Get-Rich-Quick Promises
- Be cautious of companies or individuals promising quick, high returns, especially in crypto. Reliable investments don't guarantee fast profits.
- Ignore "Investment Managers" Who Contact You
- Any "investment manager" claiming they can rapidly grow your money is likely fraudulent. Trust only well-researched, regulated firms.
- Beware of "Celebrity" Endorsements
- Real celebrities won't directly contact you for crypto investments. Scam accounts often impersonate public figures to gain trust.
- Verify Online Romantic Connections
- Meet online romantic interests in person before sharing any personal information or money. Scammers often target dating platforms.
- Avoid Suspicious Links in Messages or Emails
- Messages claiming account issues and offering "support" are usually scams. Access your accounts only through official channels.
- Contact Regulators Directly for Financial Alerts
- If you receive a message from a government or financial entity claiming account issues, contact them directly via their official website.
- Be Skeptical of Job Offers Related to Crypto
- Ignore job postings for roles like "crypto miner" or "cash-to-crypto converter." Many of these roles are fronts for money-laundering schemes. Additionally, if you receive "moderator" or "marketing manager" positions saying they will pay $1000 per week, those are scams, don't even entertain them or you'll end up on their list and more will contact you later.
- Report Blackmail Demands for Crypto Payments
- If someone claims to have compromising information and demands crypto payments, report it immediately. Blackmail is a common scam tactic.
- Decline "Free" Money Offers
- Offers of free crypto or money are almost always scams. Legitimate entities don't give out money without clear requirements.
IV. BONUS: 20 Crypto Red Flags to Watch out for
- Guaranteed high returns with minimal risk is often a ploy to lure investors into crypto scams.
- High-pressure tactics to "act quickly" are commonly used to trap victims in fraudulent investments.
- Unsolicited messages about investment opportunities should be ignored as they often signal scams.
- Requests for private keys or seed phrases are an immediate red flag, as these should never be shared.
- Celebrity endorsements of crypto projects are frequently faked to create a false sense of trust.
- Anonymous team members and the inability to verify project leaders online suggest a lack of legitimacy.
- Missing or vague technical documentation indicates the project may be poorly planned or fraudulent.
- Unrealistic claims of massive profits often signal a scam and should be approached cautiously.
- Locked or restricted liquidity can limit your ability to cash out, raising concerns about potential fraud.
- Excessive marketing without substantive details often indicates that the project may be more hype than reality.
- Promises of steady returns, regardless of market fluctuations, are unrealistic and signal possible fraud.
- If sellers lack proper financial licenses or regulatory registration, proceed with caution as this could indicate a scam.
- Disguised token sale progress, such as using private addresses, makes it difficult to verify funding and should be viewed suspiciously.
- Lack of consistent updates and transparency about project progress on official channels is a major red flag.
- Duplicate or lazy imitation of features from popular projects indicates potential low-value or scam intentions.
- Missing or flawed legal documents, financial models, and planning resources in the whitepaper suggest a weak project.
- Sudden, unexplained price spikes could signal market manipulation and are worth investigating.
- Low-value coins priced at fractions of a cent are often highly volatile and easily manipulated.
- Emails with poor grammar or urgent requests for personal information usually indicate phishing attempts.
- Unverified job listings for "crypto miners" or "cash-to-crypto converters" often serve as fronts for money-laundering schemes.
V. Trade Safely with TOKERO
TOKERO employs advanced security protocols to protect your transactions. This includes end-to-end encryption, secure storage solutions, and continuous monitoring for suspicious activities.
To ensure the highest level of security, our platform undergoes frequent security evaluations by renowned third-party blockchain security experts. These assessments help uncover and rectify any vulnerabilities, keeping our systems aligned with the most current security protocols and standards.
We also take it one step further, as our dedicated support team is available 24/7 to assist you with any security concerns. Additionally, TOKERO Academy provides educational resources, including webinars and courses, to help you stay informed about the best security practices.
VI. Conclusion
We're all navigating the exciting but sometimes daunting world of cryptocurrencies together, and it's perfectly normal to feel overwhelmed by the security challenges that come with it. Whether you're just starting or you're a seasoned investor, remember that protecting your digital assets doesn't have to be complicated – it's about building good habits one step at a time as long as with each step you add a new layer of security.
Think of this guide as your friendly companion on the journey to crypto security. While we can't eliminate every risk in the digital world, we can definitely stack the odds in our favor by following some straightforward precautions. Take your time implementing these security measures, and don't hesitate to revisit them whenever you need a refresher. After all, your peace of mind is just as valuable as your investments.


